
Modern organizations rely heavily on the seamless and secure functionality of web applications. Unfortunately, small and large businesses don’t prioritize security testing of their web applications. As a result, attackers can easily
compromise these applications, disrupt business operations and gain unauthorized access to sensitive data. As many organizations wrongly rely on the accuracy of automated web application security scanners, they end up with unidentified flaws in their applications’ functionality, source code, and infrastructure.
What is web penetration testing ?
Conducting a web penetration test involves a systematic process, including
enumeration of the target application, identification of vulnerabilities and exploitation of
vulnerabilities that could be used to compromise an application. During a test
web intrusion, a pentester evaluates the security of an application by exploiting it, as would a
attacker. For example, the specialist will examine how an unauthorized person could
access sensitive application data.
To this end, a web application penetration test helps organizations find vulnerabilities in
security in applications that adversaries could easily exploit. At least one
Penetration testing of a web application includes checks for the following vulnerabilities
(included in OWASP Top 10 Web Application Security Risks):
• Failing access control
• Cryptographic failures
• Injection
• Insecure design
• Misconfigured security
• Vulnerable and obsolete components
• Identification and authentication defects
• Software and data integrity defects
• Failures in recording and security monitoring
• Server-side forged queries
How do we carry out a web penetration test ?
Web application penetration tests are security assessments intended to analyze
architecture, design and configuration of web applications. Our team uses
advanced web application security skills to perform security testing
Manual and in-depth penetration of modern web applications. In addition, we offer
code-assisted penetration testing to explicitly understand the application, detect
deep problems in the source code and reduce the number of false positive results.
At Offensive Fox, we use the following testing methodologies:
OWASP Top 10 (et au-delà !)
OWASP ASVS
Guide de test de l’OWASP
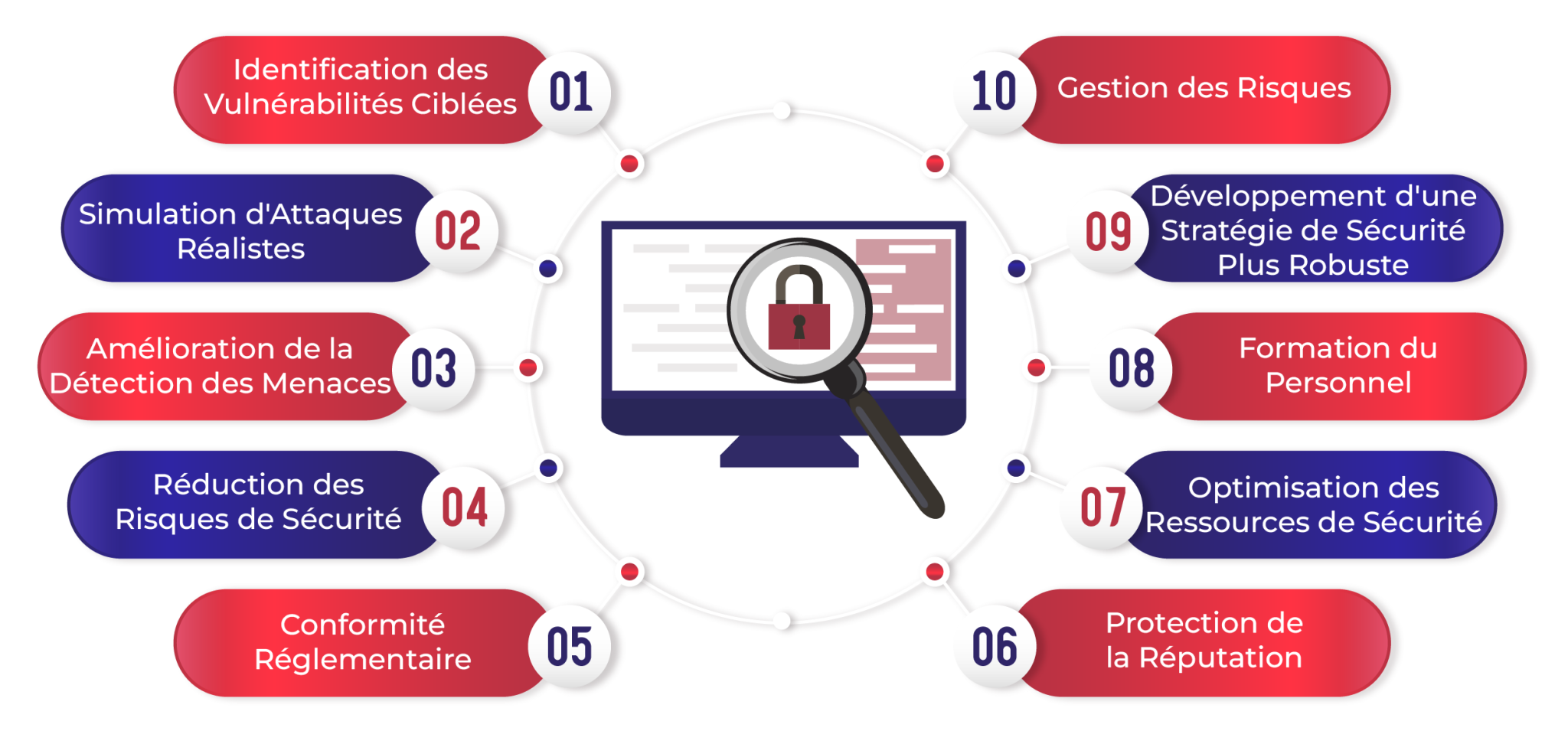
Benefits of a web penetration test
Be prepared to defend your business with our cybersecurity expertise. Your online security is our priority.
Stay informed ! Subscribe to our newsletter to receive the latest cyber security tips
Copyright ©2024 Offensivefox | Created by Devtitechnologie | Web agency specializing in the creation of professional websites