Most businesses prioritize defending the perimeter of their environment against external threats. But what happens if this perimeter is violated?
The foundation of your organization’s security posture should be a secure, robust infrastructure. As technology advances, hackers are developing more complex strategies to breach an organization’s security defenses and cause damage. . Preparing for this growing threat requires thinking like an adversary. And the best way to do this is to perform an internal network penetration test.
What is an internal penetration test ?
An internal penetration test is an advanced infrastructure assessment that evaluates the extent of a security vulnerability to internal attacks or an adversary who has already gained a foothold in a network and is looking to increase their privileges. This type of test evaluates what an attacker could achieve with initial access to a network. They are more detailed than automated vulnerability scans and aim to gain access to sensitive assets on the internal network. An internal penetration test involves privilege escalation, deploying malware, MITM attacks, lateral movement, exfiltration of sensitive data, and other malicious activities.
At a minimum, the following steps are involved:
How do we conduct an internal penetration test on a network ?
Our team goes beyond traditional vulnerability assessments and often provides objective-based assessments based on the scope of work. This includes, but is not limited to, obtaining domain administrator privileges or obtaining highly sensitive data within the internal network. We recommend conducting internal network penetration tests frequently to discover vulnerabilities and help remediate them, given the financial implications of an exploit. Our approach to internal penetration testing includes (but is not limited to) the following:
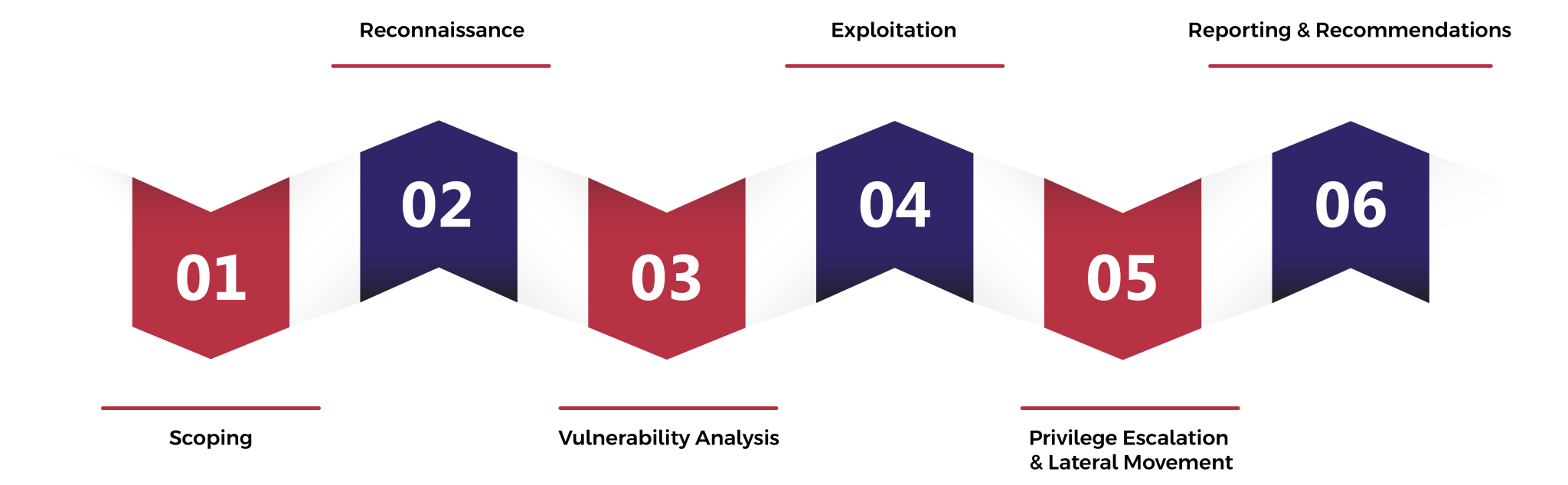
Scoping
We work closely with you to define the scope of the test, including target systems,
the desired testing methodologies and any specific compliance requirements.
Reconnaissance
Our experts collect information about your internal network infrastructure in order to
understand the layout, devices and potential entry points.
Vulnerability Analysis
We perform an in-depth analysis of your network infrastructure, including systems,
applications and databases, to identify known vulnerabilities and bad ones configurations.
Exploitation
Our ethical hackers simulate real attack scenarios to exploit vulnerabilities
identified and gain unauthorized access to your internal systems.
Privilege escalation & lateral movement
We assess the potential for attackers to escalate privileges and move laterally
within your network to identify weaknesses in access controls and segmentation.
Report & recommendations
We provide a comprehensive report detailing the vulnerabilities discovered, their potential impact
and practical recommendations for remediation. Our team can help you implement
the security measures needed to improve the resiliency of your network.
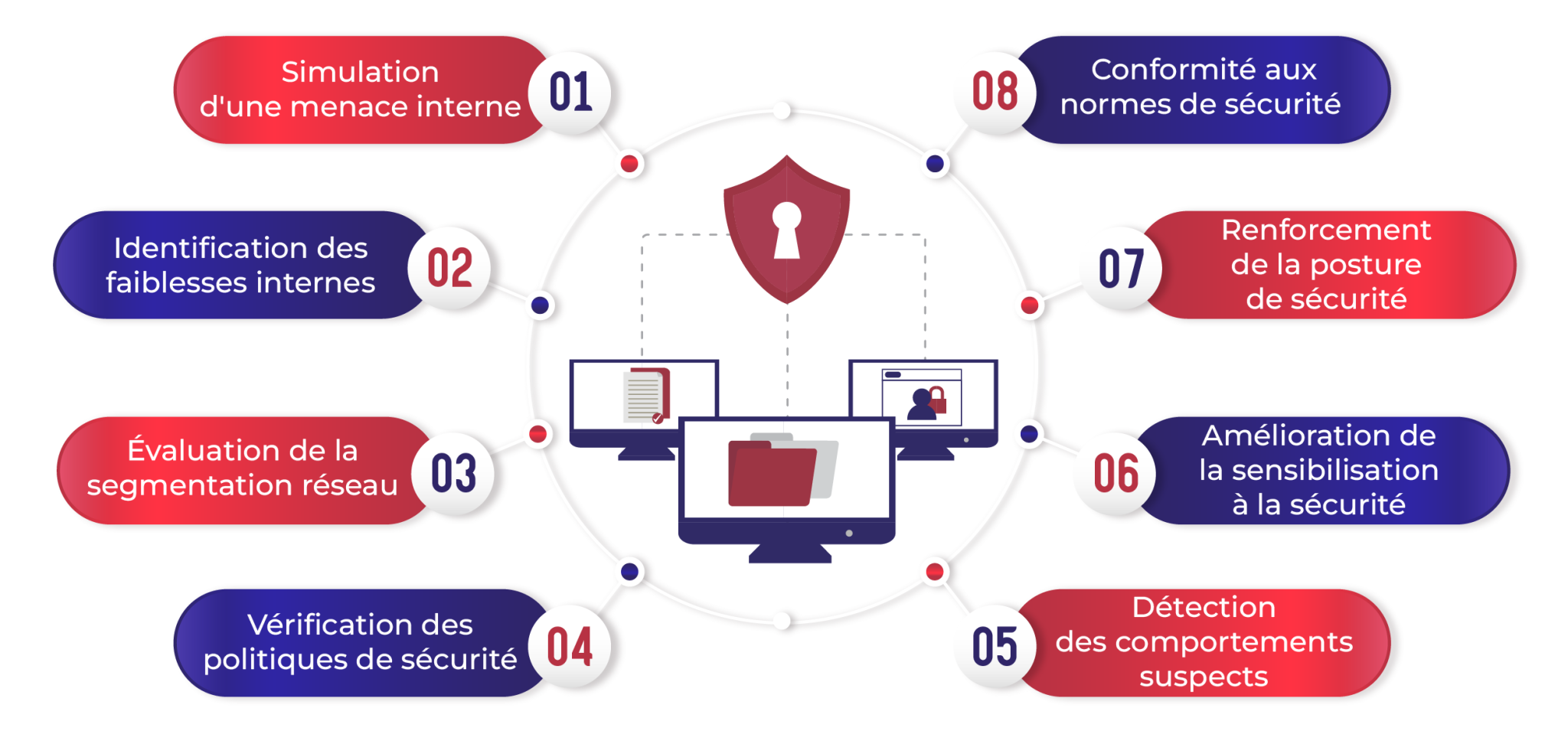
Benefits of an internal penetration test
Be prepared to defend your business with our cybersecurity expertise. Your online security is our priority.
Stay informed ! Subscribe to our newsletter to receive the latest cyber security tips
Copyright ©2024 Offensivefox | Created by Devtitechnologie | Web agency specializing in the creation of professional websites