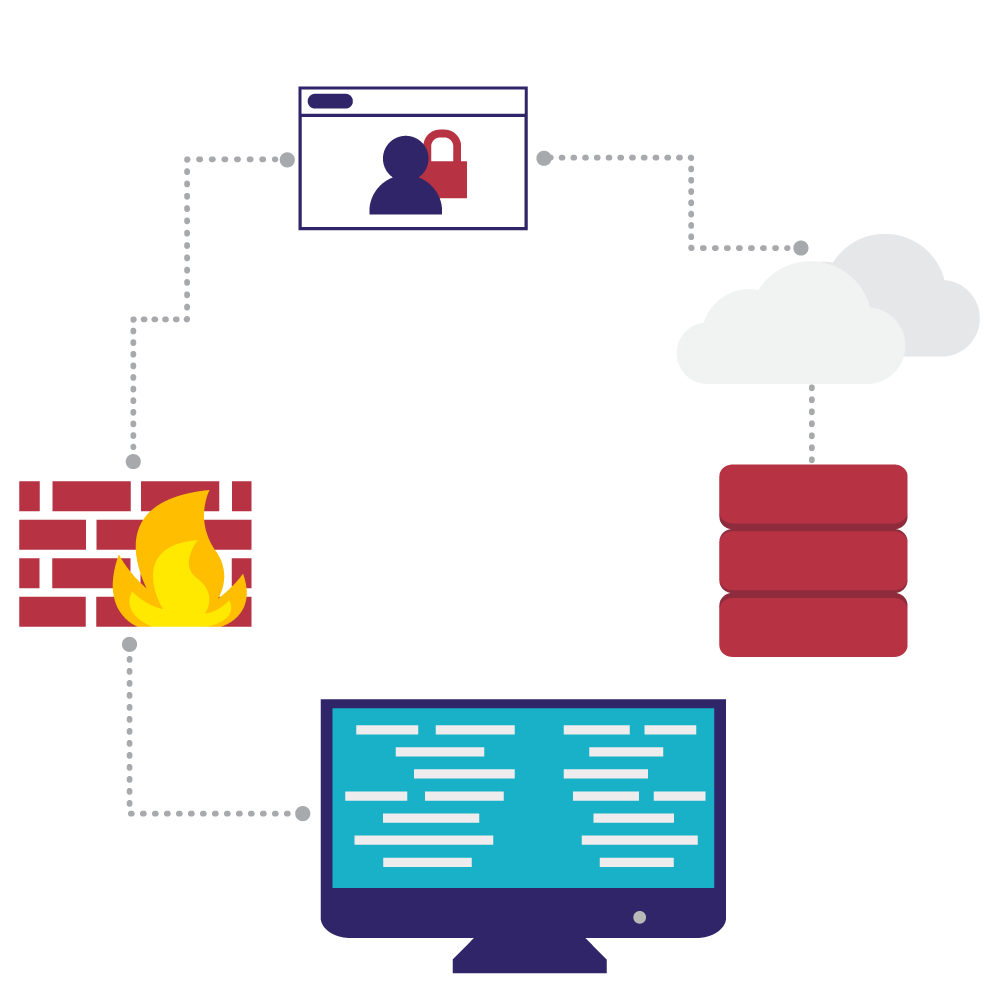
If your company’s network perimeter is not properly configured, patched, and maintained, it can be exposed to breaches. It is essential to have specialized skills to
secure your internet-facing infrastructure. This includes operating systems, cloud services, servers and firewalls.
External penetration testing of your network can help identify security vulnerabilities that unauthorized individuals can exploit to gain access to, destroy, or exploit your critical business data.
What is external penetration testing ?
An external intrusion test makes it possible to identify weaknesses in the security perimeter, to discover
publicly accessible vulnerable systems and exploit these systems. These assessments can
focus on a particular IP range or on in-depth searches using search techniques.
open source intelligence (OSINT). These tests also make it possible to map the
attack paths that lead to internal assets and validate firewall configurations in order to
reduce the overall attack surface. The main objective of these tests is to discover the flaws of
security in your external infrastructure.
How we carry out an external penetration test
At Offensive Fox, an external penetration test reveals security vulnerabilities that attackers
can be exploited to steal company data. Our comprehensive reports cover encryption,
patches and other vulnerabilities while examining an organization’s preparedness against
external network violations. We use a sophisticated penetration testing methodology
to assess an organization’s external security posture. Our approach to penetration testing
external includes (but is not limited to) the following
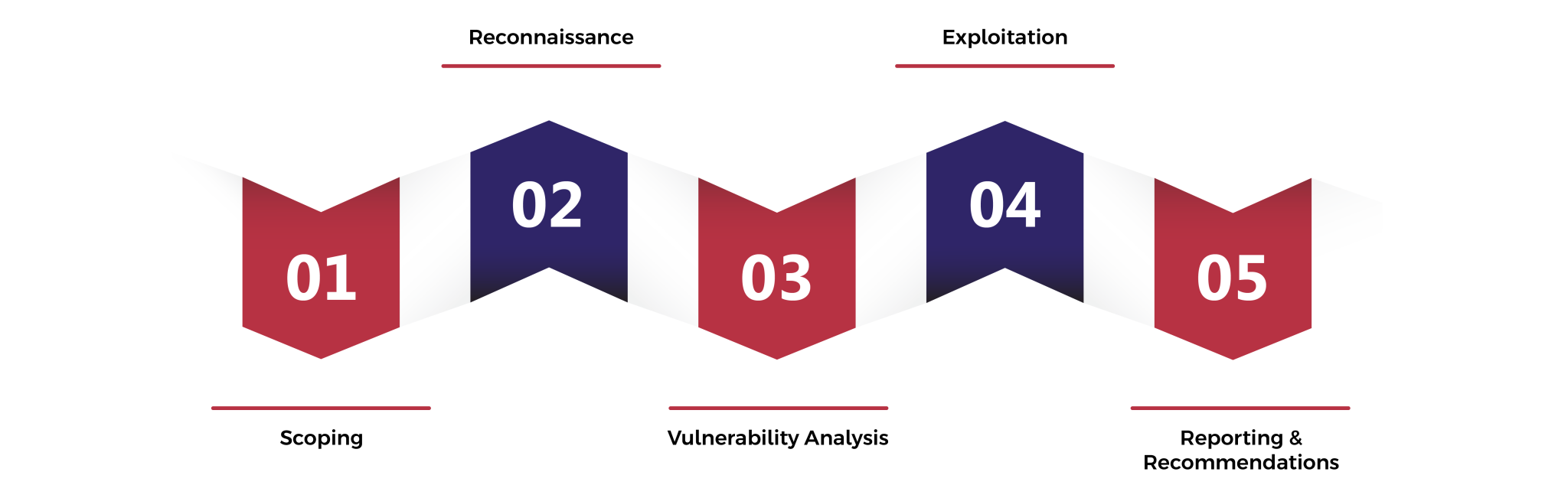
Scoping
We work closely with you to define the scope of the test, including target systems,
the desired testing methodologies and any specific compliance requirements.
Reconnaissance
Our experts collect information about your internal network infrastructure in order to
understand the layout, devices and potential entry points.
Vulnerability Analysis
We perform an in-depth analysis of your network infrastructure, including systems,
applications and databases, to identify known vulnerabilities and bad configurations.
Exploitation
Our ethical hackers simulate real attack scenarios to exploit vulnerabilities
identified and gain unauthorized access to your internal systems.
Report & recommendations
We provide a comprehensive report detailing the vulnerabilities discovered, their potential impact
and practical recommendations for remediation. Our team can help you implement
the security measures needed to improve the resiliency of your network.
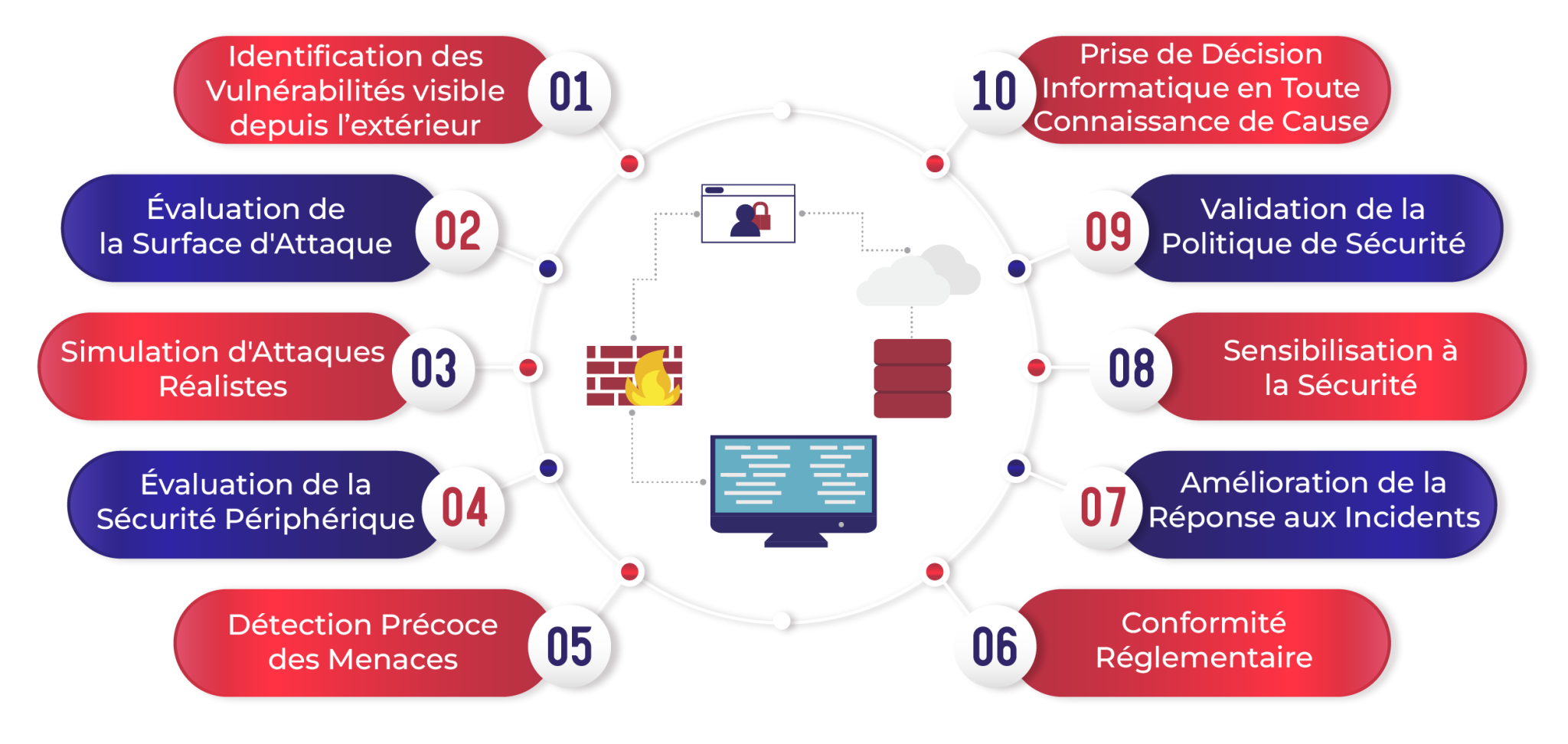
Benefits of an external penetration test
Be prepared to defend your business with our cybersecurity expertise. Your online security is our priority.
Stay informed ! Subscribe to our newsletter to receive the latest cyber security tips
Copyright ©2024 Offensivefox | Created by Devtitechnologie | Web agency specializing in the creation of professional websites